I found a phishing filter (here) which can be used in content blockers (as well as adblockers) like uBlock Origin. I wanted to analyze the phishing links — and this is the analysis.
Popular Web Hosts
Who are the web hosts (and website builders) that are used the most often in the phishing websites examined?
Google for Firebase Hosting, with
2,428unique websites 1.Weebly (a free website builder), with
2,239websites. 2r2.dev, with
1,286entries.
This refers to the R2 file storage offered by Cloudflare®.crazydomains.com (with their Sitebeat website builder), with
1,164websites.
Interestingly, the domains I tested seemed to redirect toglobal_errors.sitebeat.crazydomains.comwith a “Coming Soon” page (which is also in the filter list)workers.dev (Cloudflare Workers), with
759entries
Cloudflare Workers is a service which allows a user to run JavaScript on their edge nodes. I presume these could be proxies or returning hardcoded HTML. However, the code isn’t visible so that’s just speculation.
Just these 5 domains cover 66% of recognized hosting providers.
Dynamic DNS
Dynamic DNS is a service where a fixed hostname maps to a dynamic IP address (like a home IP address) that updates regularly.
Documents
This category consists of platforms that host documents, spreadsheets and presentations.
Google Docs, with
1,296entries.
This includes 74 forms, 10 documents, 6 drawings, and 1,206 presentations.
Almost all presentations contain “/pub?” with some data as URL parameters. I’m not too sure what this does.
In addition, Google Drive has9entries.
Many of the URLs seem to be taken down, either by the owner or by Google.telegra.ph, with
3entries.notion.site, with
2entries.
Forms
This consists of tools that allow users to build forms.
Microsoft Forms, with
62forms.forms.app, with
24forms.Google Forms (forms.gle), with
15forms.JotForm, with
11forms.formstack.com and hsforms.com, with
7forms each.
Scripts
There are 102 entries for “script.google.com” (Google Apps Script) which link to macros and running the script, sometimes with parameters to track the user that clicks.
Government
There are 4 government domains, none of which seem inherently malicious. The entire domain is blocked by the phishing filter.
I’m not listing these domains here because the pattern is what matters, not an individual country.
IP Addresses
98 unique IP(v4) addresses (with 441 entries) exist in the phishing filter list.
(For the below information, ipinfo.io was used as a source)
Top ASNs
ASNs (Autonomous System Numbers) are the organizations that own a block(s) of IP addresses to provide services to their customers (hosting providers, ISPs, some VPNs)
“AS132203 Tencent Building, Kejizhongyi Avenue” with
46IP addresses.“AS14061 DigitalOcean, LLC” and “AS16276 OVH SAS” with
5IP addresses each.“AS396982 Google LLC” with
4IP addresses.
Top Cities
Singapore with
40IP addresses.Santa Clara (California, US) with
9IP addresses.Beauharnois (Quebec, Canada) with
4IP addresses.
Link Shorteners
TinyURL, with
176entries.Bitly, with
161entries.Twitter’s link shortener (t.co) with
160entries.s.id with
115entries.t.ly with
33entries.
IPFS
IPFS is a Web3 technology that allows decentralized hosting of files. These are not directly accessible in a browser, but through gateways like those from Cloudflare, ipfs.io and others.
When I saw the numbers for IPFS, I was genuinely surprised.
From Cloudflare IPFS alone, there are
5,380entries. 3 (I also want to point out that BleepingComputer has an article about Cloudflare’s IPFS gateway being used for phishing attacks, showing its prominence.)ipfs.io with
990entries.nftstorage.link with
805entries.dweb.link with
416entries.Infura IPFS with
366entries.
Evasion Methods
These are methods used such that the domain seems innocent but leads to another website (not including link shorteners).
VKontakte, with
39entries – this uses an “away” page that redirects to another website (an account on VKontakte is required).google.com, with
22entries4 with 13 URLs having the path “/url?q=[insert a url-encoded url here]” and9entries using AMP to have a Google domain, but with a phishing page. They’re having their cake and eating it too.translate.goog (Google Translate for websites), with
15entries.accounts.google.com, with
8URLs, all of which contain “continue=” and “followup=” with URLs as the values. This redirects the user after they’re signed in.
Uncategorized
There are 6,593 uncategorized domains.
3058domains use a “.com” TLD.437domains use a “.top” TLD.217domains use a “.br” TLD.200domains use a “.net” TLD.186domains use a “.pl” TLD.176domains use a “.xyz” TLD.108domains use a “.org” TLD.
The Big Picture
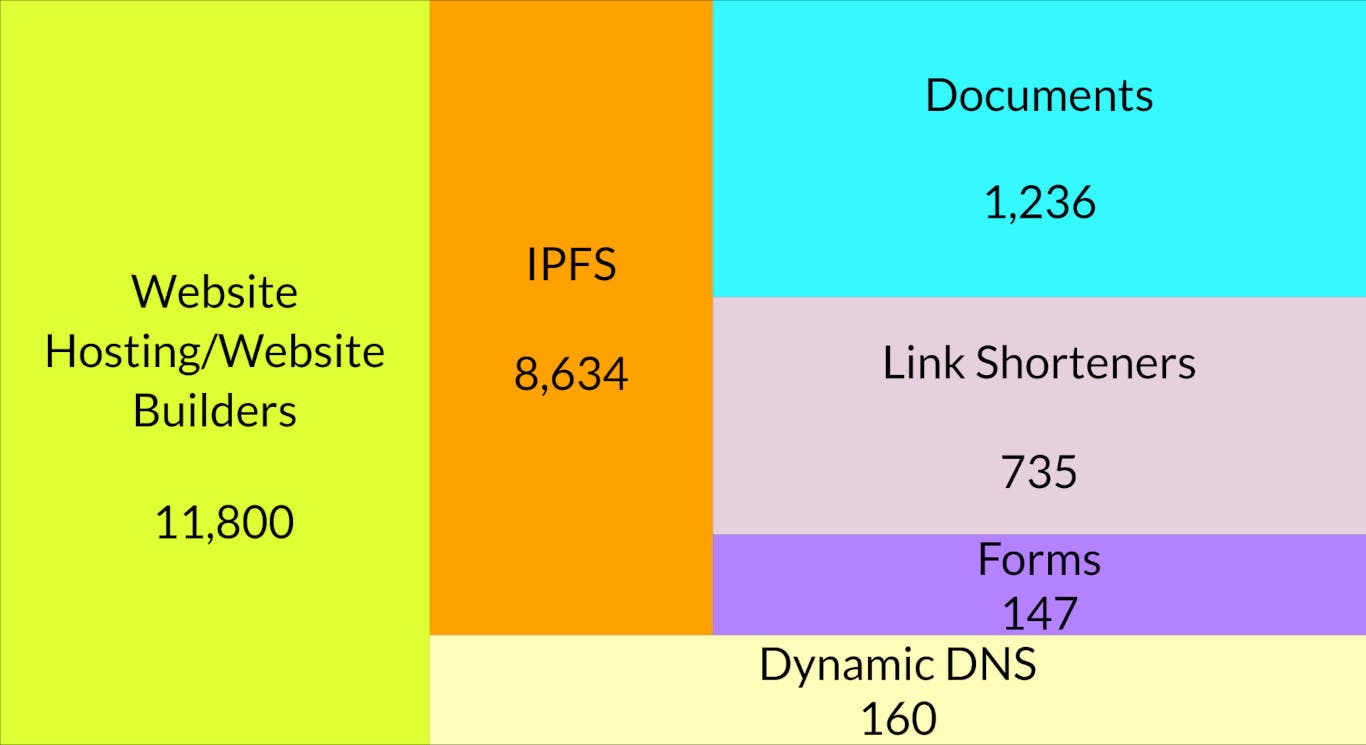
The filter list has more than 2,100 entries for both
firebaseapp.comandweb.app, due to the data sources of the filter list including both domains. Websites on both domains have been filtered down to just one, leading to the lower number. ↩Weebly has two domains which are
weebly.comandweeblysite.comfor hosted websites, in which none of the entries are duplicates. ↩This is across two domains (
cf-ipfs.comandcloudflare-ipfs.com) with duplicate addresses removed. ↩︎There were
23entries, but one of them was a search, so that’s been excluded. ↩

